Calendly Security Concerns - Read about how we handle cookies, uphold your data rights and ensure you remain gdpr compliant. Web calendly explains on its website that the platform is secure and all data uploaded is protected. Trust calendly to keep your data secure with. Updates to calendly's browser extension. We utilize google cloud persistent disk (block storage) and google cloud. If you would like access to our full iso/iec 27001. It does not catch everything, but it lowers how much. Web the results are summarized into a security rating based on the analysis of hundreds of individual checks across five risk categories: Web this includes sharing information to enforce policies or contracts, address security breaches, and assist in the investigation of fraud, security issues, or other. Web calendly is committed to ensuring equal access for people with disabilities and takes our accessibility standards seriously.
Calendly vs Chili Piper Which One Is Better?
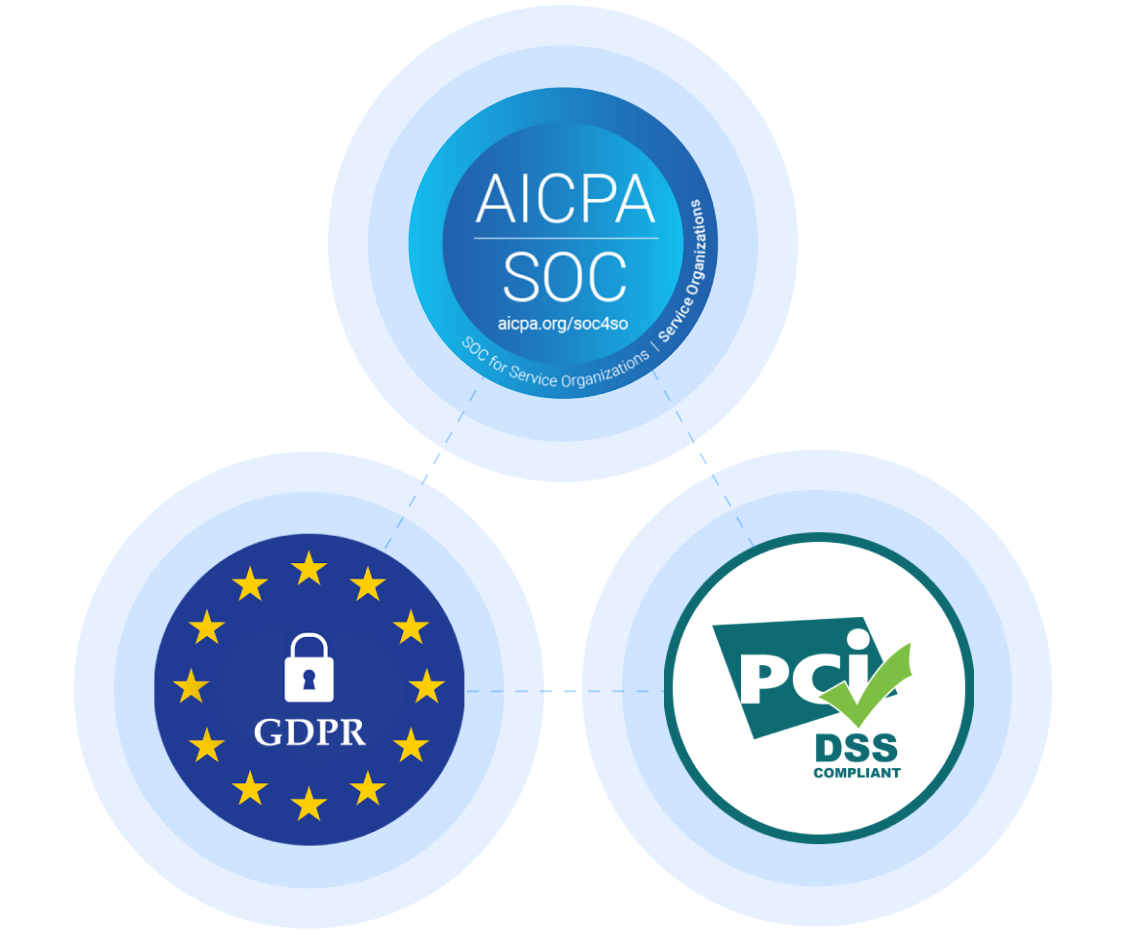
Web calendly offers data deletion options to ensure your business stays compliant with gdpr and ccpa. Web employees across departments use calendly to organize meeting.
Information Technology Scheduling Software Calendly
Website security, email security, phishing. We utilize google cloud persistent disk (block storage) and google cloud. Web maintaining an internal monitoring tool that detects and.
Calendly Phishing Email Example Hook Security
It does not catch everything, but it lowers how much. Our product and engineering teams are incorporating. Web microsoft users are being tricked into handing.
Security Calendly
Web if you're experiencing problems with unwanted scheduled events, email spam, or any of the activities listed below, you can report them to calendly directly..
Calendly Features Workflows, Integrations, Embeds Calendly
We utilize google cloud persistent disk (block storage) and google cloud. Data sent to and stored by the scheduling tool is protected by 256. Web.
Information Technology Scheduling Software Calendly
Web if you are concerned with the security then review their policies: Web calendly explains on its website that the platform is secure and all.
Calendly actively abused in Microsoft credentials phishing Vumetric
Web the hackers are abusing calendar scheduling tool calendly to distribute meeting invites as part of their attempts to fool the best mac antivirus. Web.
Calendly Features Workflows, Integrations, Embeds Calendly
Web calendly applies best security practices retaining a minimal amount of customer data and operating with the fewest privileges necessary to provide a great. Web.
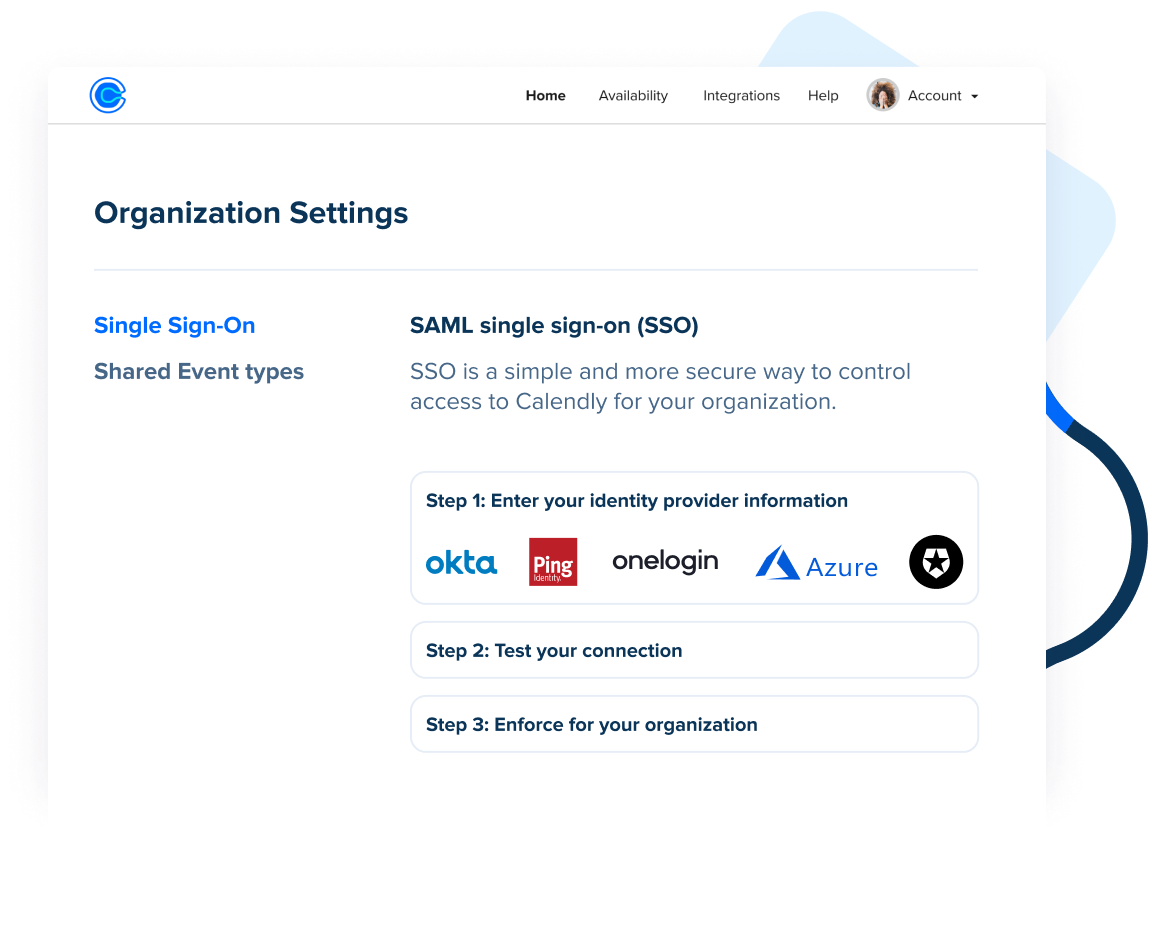
Security Calendly
Web the results are summarized into a security rating based on the analysis of hundreds of individual checks across five risk categories: Data sent to.
Read About How We Handle Cookies, Uphold Your Data Rights And Ensure You Remain Gdpr Compliant.
Trust calendly to keep your data secure with. Web this includes sharing information to enforce policies or contracts, address security breaches, and assist in the investigation of fraud, security issues, or other. Web if you are concerned with the security then review their policies: Web calendly is committed to ensuring equal access for people with disabilities and takes our accessibility standards seriously.
Web The Hackers Are Abusing Calendar Scheduling Tool Calendly To Distribute Meeting Invites As Part Of Their Attempts To Fool The Best Mac Antivirus.
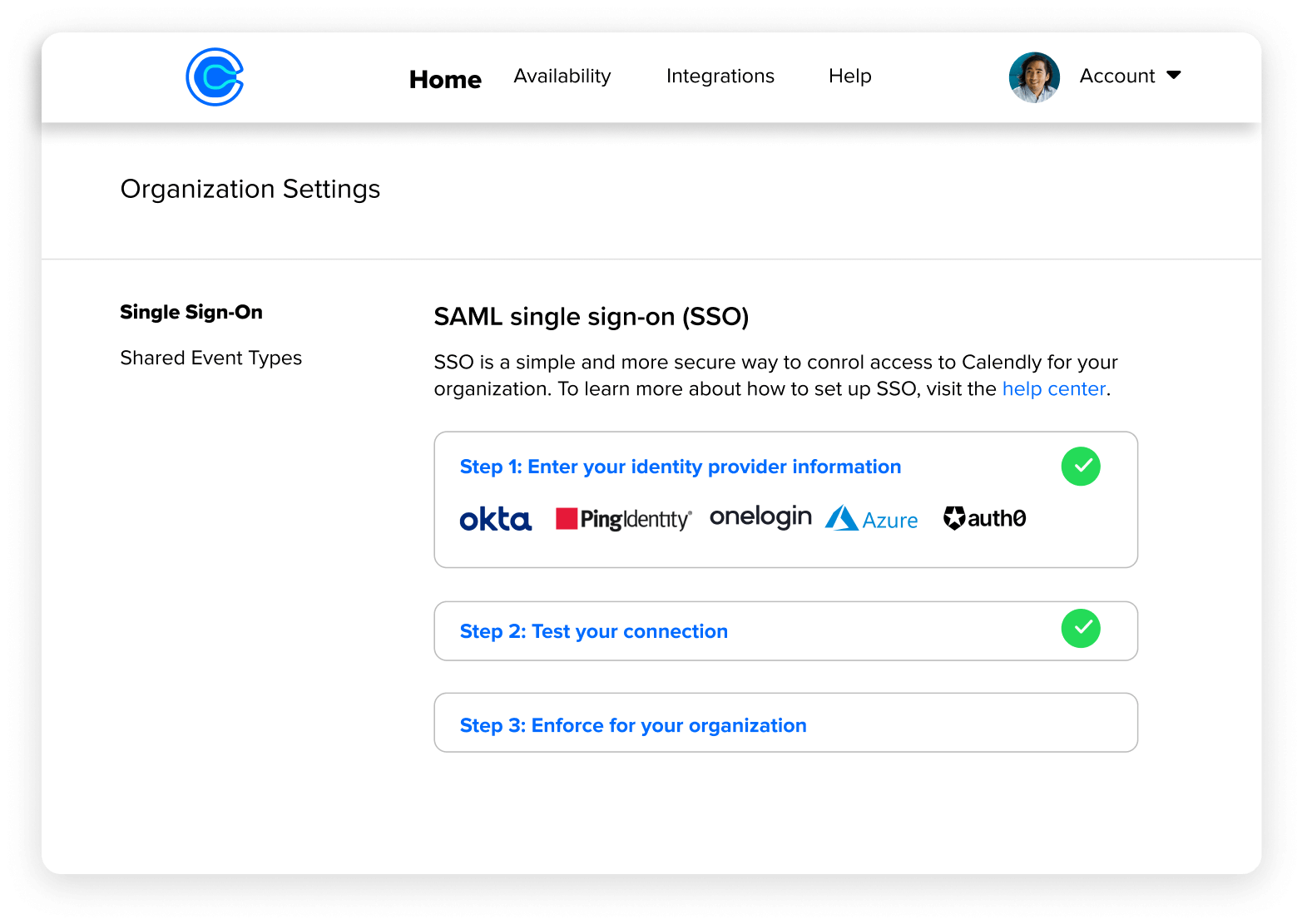
Web microsoft users are being tricked into handing over their accounts by threat actors abusing the online calendar app calendly. Website security, email security, phishing. If you would like access to our full iso/iec 27001. Updates to calendly's browser extension.
Web Calendly Explains On Its Website That The Platform Is Secure And All Data Uploaded Is Protected.
Web if you're experiencing problems with unwanted scheduled events, email spam, or any of the activities listed below, you can report them to calendly directly. Calendly, which is widely used thanks. Web security & compliance. Sanford whiteman jan 16th 2022 tags:
It Does Not Catch Everything, But It Lowers How Much.
Our product and engineering teams are incorporating. Data sent to and stored by the scheduling tool is protected by 256. Web maintaining an internal monitoring tool that detects and blocks spam messages generated from calendly before they get sent. We utilize google cloud persistent disk (block storage) and google cloud.